Generic Malware Debunking Post
Yup, I’m about to do another blog post where someone says that a website is clean but it doesn’t look like it to us. I did a very similar post in January 2007, and in that post I said I’ve checked out a quite a few “we don’t have any malware” reports at this point, and I’ve yet to see a false positive — the sites in question have each had some malware on them.
In fact, just last week I handled a very similar case where Google proactively reached out to a website that had a scripting flaw security. The deja vu from my January 2007 post plus the situation last week made me want to write a generic malware debunking post. Are you ready? Here we go:
$ACCUSER = Brett Glass
$FORUM = Dave Farber’s Interesting People mailing list, specifically this email.
$LONG_ACCUSATION = (I’m going to quote Brett’s whole email here, just for context)
Everyone:
Google has been a strong supporter of the agenda of Free Press, an
inside-the-Beltway lobbying group which has spent hundreds of
thousands of dollars lobbying for regulation of the Internet under
regime known as “network neutrality.” While some of the tenets
included in this agenda are not reasonable, one of those that IS
reasonable is the notion that large corporations such as Comcast
should not block content with which they disagree.
However, Google -- itself a large corporation -- appears to be
blocking a site which expresses opinions with which it does not
agree on this very issue. When one does a search for the terms
“neutrality” and “site:pff.org” (the link
http://www.google.com/search?hl=en&q=neutrality+site%3Apff.org&btnG=Google+Search
will perform this search for you), many of the pages and documents
on the site -- in particular, white papers expressing views with
which Google disagrees -- are tagged with a warning that “This site
may harm your computer.” One cannot click through to the documents
and pages in Google’s search results without cutting the URL from
the page and manually pasting it into one’s browser.
The Web site, operated by a group known as the “Progress and
Freedom Foundation,” does not appear to contain any malware. When
one queries Google as to why the site was blacklisted, it claims
that “Part of this site was listed for suspicious activity 1
time(s) over the past 90 days.” Yet, we could find no malware or
other exploits in the blacklisted PDF files, some of which contain
very well presented and cogent arguments against the agenda which
Google has been actively supporting.
Could it be that Google (whose motto is, reportedly, “Don’t be
evil,”) saying, “Do as I say, not as I do?”
--Brett Glass
P.S. -- What’s especially interesting is that if one queries Google
using just the term, “site:pff.org” (you can use the link
http://www.google.com/search?hl=en&q=site%3Apff.org&btnG=Search
to do this query), one can see that the majority of the supposedly
dangerous site is not blocked. But most or all of the documents
expressing viewpoints on “network neutrality” are.
$SHORT_ACCUSATION = “Google blocked a site with opinions that it disagrees with. Worse, the query [site:pff.org] seems to show that only urls under pff.org/issues-pubs/ are labeled as potentially harmful, and that is the directory where many of the documents that disagree with Google are.”
Given what we have so far, my generic debunking would begin like “Dear $ACCUSER, I saw on $FORUM where you mentioned that Google is flagging a website as malware. You said that $SHORT_ACCUSATION. I wanted to give you a little more background and context to let you know that Google did see an actual malware attack via a real security hole. The other thing you need to know is that Google flagged the site because of the security hole, not because Google agrees or disagrees with any particular content on the site.”
Then I’d give a little background history on all the different ways that Google helps users and webmasters avoid malware. Most of the background would come from this overview post. Since that post was published in mid-2007, Google has done even more to protect users:
- Niels Provos and his colleagues published another technical report with more details about the malware detection framework and what it discovered (more info here).
- Google launched a Safe Browsing API so that third party applications can benefit from Google’s list of malware and phishing urls. If you appreciate that Firefox 3 has better security, one of the reasons is that Firefox 3 utilizes the Safe Browsing API.
- More recently, the anti-malware folks at Google launched a Safe Browsing Diagnostic page where you can enter a url and get a ton of really useful information.
The last one is especially impressive. For example, check out the Safe Browsing Diagnostic page for pff.org:
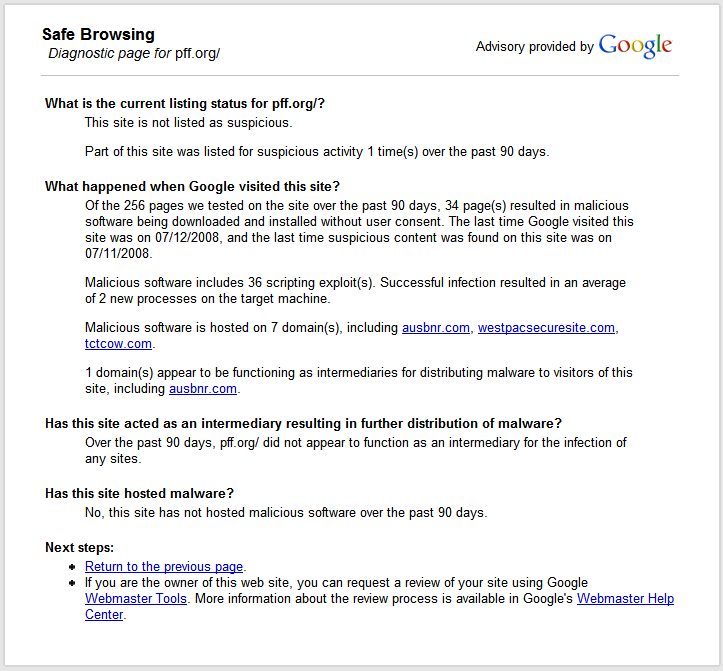
That page gives a ton of helpful info to site owners and anyone else who is interested in why a particular site or url was flagged as potentially harmful.
All that would go quite far to reply to people that had questions about their site being flagged for malware. But this post is getting quite long, so let’s get back to this specific report in this case. The original person who reported this situation had already noticed that not all of pff.org was flagged. If you do a site: query on Google, you only see warnings for pff.org/issues-pubs/ .
If you visit pff.org/issues-pubs/, you’ll see that it’s a web form. It looks like pff.org stored their data in a SQL database but didn’t correctly sanitize/escape input from users, which led to a SQL injection attack where regular users got exposed to malicious code. As a result, normal users appear to have loaded urls like hxxp://www.ausbnr .com/ngg.js and hxxp://www.westpacsecuresite .com/b.js
www.mattcutts.com
published @ September 1, 2008